Containerize Your AI Workflow
RhinOS 26
Secure Enterprise
NAS Operating System

RhinOS powers Ciphertex SecureNAS® systems in mission-critical environments, delivering military-grade security, ZFS data integrity, and modern container-based extensibility — all in a simple, hardened, appliance-ready OS.
Engineered for defense, government, healthcare, forensics, energy, and enterprise deployments that demand confidentiality, integrity, and resilience at the edge and in secure data centers.
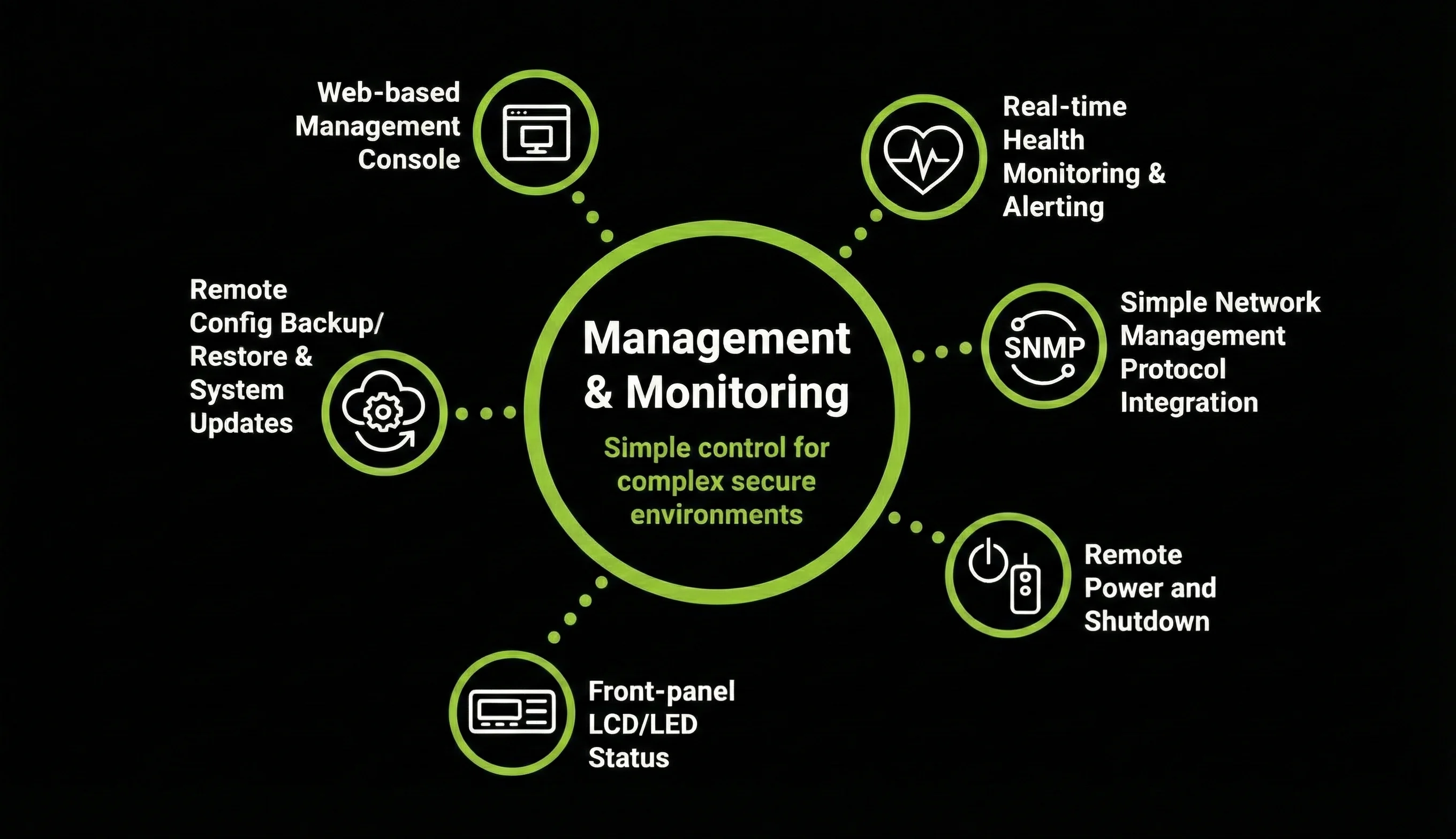
What’s New in RhinOS 26
A major security and capability upgrade
Designed for secure workloads and controlled application deployment — not a consumer app stack.
Container Support
Run approved OCI containers in a secure, isolated environment.
Docker
Local container development & deployment through Docker with embedded Portainer.
Kubernetes
Large- and small-scale container orchestration through Kubernetes.
Selectable TLS versions
TLS version selection for compliance and zero-trust environments. Support environments needing older TLS 1, and TLS 1.1 through more secure TLS 1.2 and TLS 1.3.
Enhanced firewall & access controls
Strengthened network protection and service hardening with whitelisting and blacklisting by IP and service.
Modernized Web UI
Faster administration experience and improved system visibility.
Up-to-date Security
Continual updating to protect against the latest security threats and maintain optimal operation.
Customer Benefits: Containers, Kubernetes & Enhanced Security
Modern workloads demand more than storage. RhinOS 26 transforms SecureNAS® into a secure application platform — enabling on-device analytics, automation, cyber defense tools, and modern DevOps workflows without sacrificing the hardened appliance security Ciphertex is known for.
Why Containers Matter
for Customers
Containers provide a lightweight, controlled method to deploy modern tools directly on the SecureNAS® — without modifying the OS or risking system integrity.
*Even legacy non-GPU units can run CPU-based AI inference, cyber analytics, and automation containers.
Deploy tools securely without exposing the system to untrusted packages or full OS installs.
Faster deployment cycles for new capabilities, patches, and mission-specific apps.
Run isolated workloads (forensics tools, analytics modules, AI inference engines*, cyber defense agents).
Vendor-approved execution ensures only authorized containers can run.
Zero impact to core NAS stability - containers run in sandboxed zones.
Future-proof architecture aligned with modern DevOps, automation, and edge-compute frameworks.
Benefits of Kubernetes
Integration
Kubernetes brings orchestration and scale to secure environments — even when running as a Worker Node.
What this unlocks for customers:
Distributed workloads across multiple SecureNAS® units (threat analysis, scanning, metadata tagging, microservices).
Secure participation in larger enterprise clusters without exposing the NAS OS to the public internet.
Enterprise-grade automation for container updates, failover, and scaling.
Consistent workloads from dev → test → production even in air-gapped environments.
Hybrid-edge deployments for defense, field forensics, and remote industrial sites.
RhinOS 26 brings “data-plus-compute” to the edge — securely.
Enhanced Security:
Real Operational Value
RhinOS 26’s strengthened zero-trust framework directly improves mission assurance.
Advantages to the Customer:
Security is built into every layer — hardware, OS,
container runtime, and network stack.
Selective TLS (1.0 to 1.3) ensures compatibility with legacy agencies while enabling modern, secure protocols.
RBAC + AD/LDAP ensure only the right personnel access sensitive datasets.
IP Whitelisting/Blacklisting prevents unauthorized hosts from communicating with the system.
Encrypted communication & storage protect data in motion and at rest — even in contested environments.
Hardened services reduce the attack surface for bad actors.
Container isolation prevents application-level vulnerabilities from impacting core system functions.
Security & Compliance
Confidential computing at the core
FIPS 140-2 hardware encryption key integration
Active Directory / LDAP integration
Multi-layer encryption — data at rest & in transit
TLS 1.2+ encryption (selectable protocol versions)
Secure USB port lockdown
Zero-trust principles. Military-validated hardware. Rugged security everywhere.
Role-Based Access Control (RBAC)
Built-in antivirus & firewall protection
Rapid Return on Investment
RhinOS 26 reduces integration effort, removes the need for external compute nodes for many workloads, eliminates licensing costs for common tools, and consolidates storage + secure compute into a single hardened appliance — delivering a significantly faster ROI than traditional NAS or multi-vendor deployments.
ZFS Data Integrity & RAID Protection
RhinOS delivers enterprise-grade data protection using the OpenZFS file system, ensuring fault tolerance, integrity, and
high availability in mission-critical environments.
Mirror
RAID-1
Survives 1-disk failure
Highest redundancy, high-performance reads
RAID-Z1
RAID-5
Survives 1-disk failure
General secure NAS workloads
RAID-Z2
RAID-6
Survives 2-disk failures
Mission-critical, forensic, healthcare, gov
RAID-Z3
RAID-7
Survives 3-disk failures
High-availability + high-capacity clusters
Striped Mirror
RAID-10
Survives multiple disk failures
More capacity with
higher speed
Striped Z1
RAID-50
Survives multiple disk failures
More capacity with
higher speed
Striped Z2
RAID-60
Survives multiple disk failures
More capacity with
higher speed
Striped Z3
RAID-70
Survives multiple disk failures
More capacity with
higher speed
Key Advantages
- End-to-end checksumming with automated repair
- Self-healing data paths
- Inline compression & deduplication
- Petabyte-scale expansion via VDEVs & pooling
- Up to triple-parity protection
ZFS delivers integrity, resilience, and speed far beyond traditional RAID controllers —
designed for accuracy, continuity, and regulatory compliance.
Secure Container & Kubernetes Execution
Run secure containerized services with integrated Kubernetes support — designed for controlled enterprise and mission-critical environments.
OCI container support

Kubernetes-enabled runtime
for Cluster participation

Isolated execution environment
for high-security deployments

Local container development,
testing, and deployment through
Docker and a special local
version of Portainer

Kubernetes Worker-Node
capability for secure, scaled
distributed container workloads

Deploy forensic tools, cyber
defense agents, analytics
modules & secure workloads

Preserves
appliance-grade
security posture

Optimized for secure scaled participation in Kubernetes environments — can act as a worker node in your cluster.
Enterprise File & Block Services
Flexible multi-protocol access to meet any IT workflow
Mix secure file-sharing, SAN, backup, and remote workflows seamlessly.
Virtualization & Edge Compute Support
Run controlled virtual machines for secure tasks and isolated workloads
VM support
and proprietary guest
OS options
across virtualization
platforms
Forensics, cyber tools, and system appliances — without external infrastructure.
Backup, Replication & Recovery
Built-in data durability and ransomware resilience
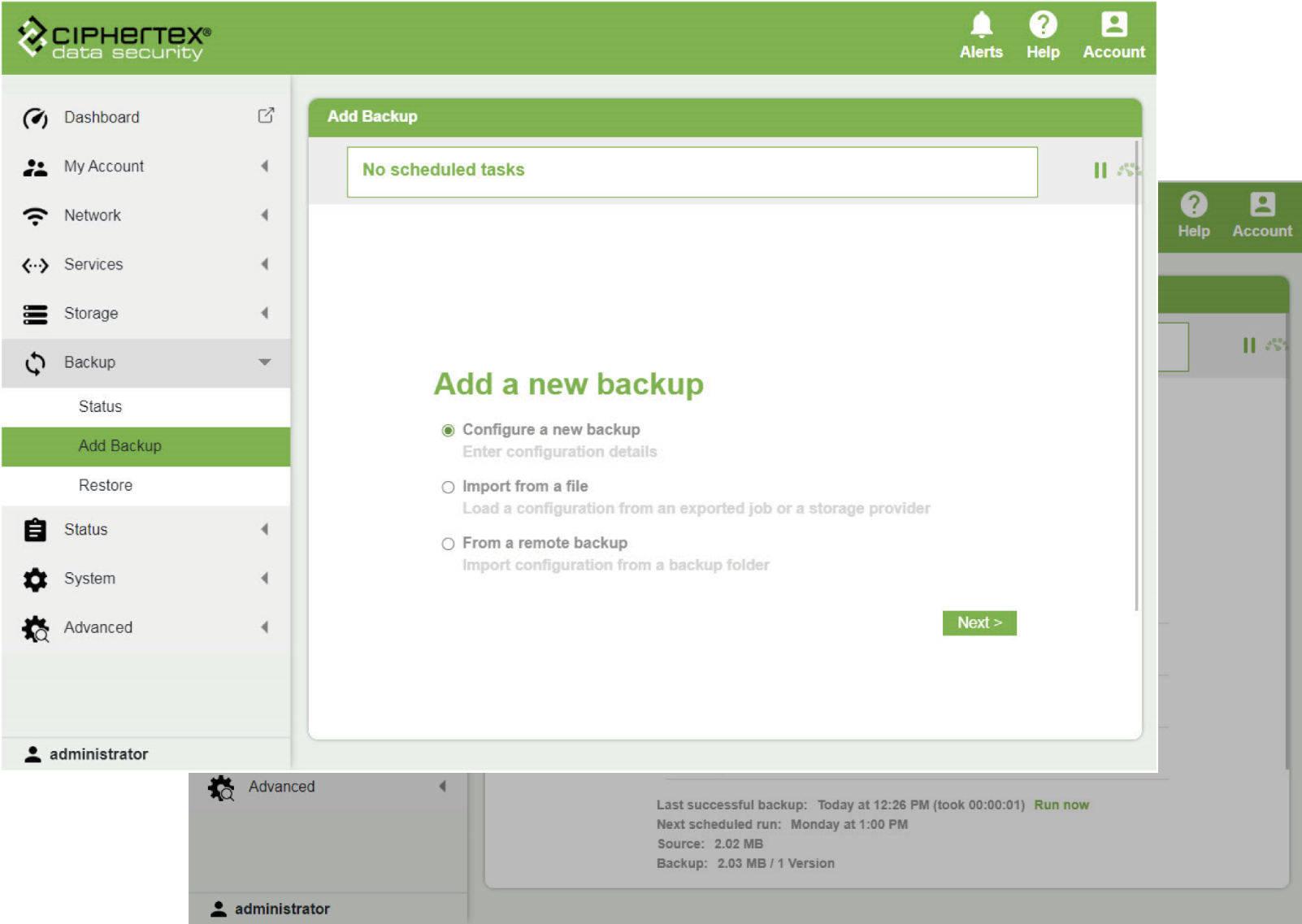
- Duplicati-based encrypted backup
- Multi-site replication
- Cloud backup targets (Azure, AWS S3,
Google Cloud, etc.) - Schedule or manual sync jobs
- USB one-touch backup
- Volume/LUN snapshots & instant
Keep mission data safe — anywhere.
Use Cases
- U.S. military & defense missions
- Federal & state government
- Law enforcement & digital forensics
- Healthcare & HIPAA environments
- Energy, oil & gas, and remote industrial sites
- Cybersecurity labs & critical infrastructure