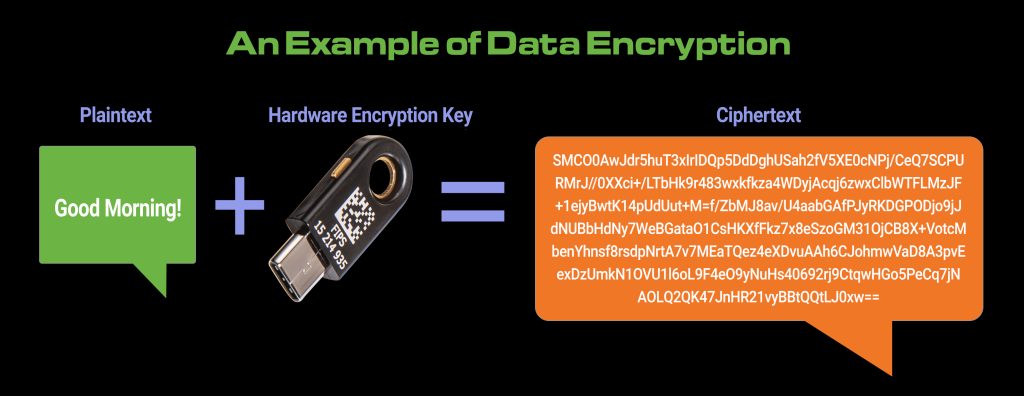
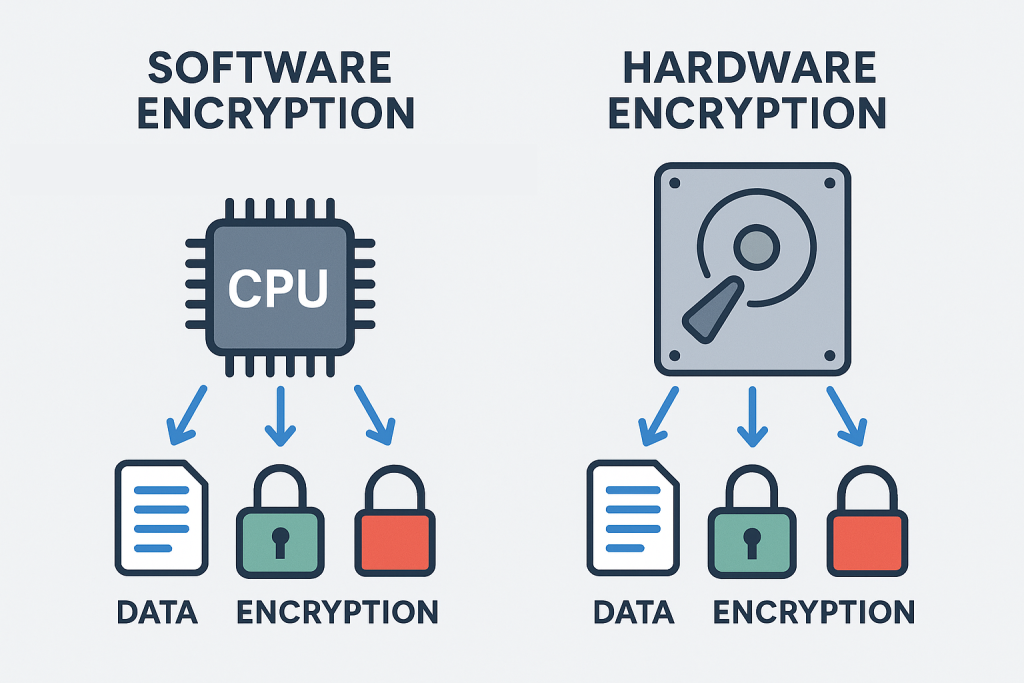
As digital systems continue to advance and expand, protecting sensitive data has become a critical priority for organizations of all kinds. Once used primarily by government agencies, encryption is now essential across industries like healthcare, defense, finance, and enterprise IT. As cybersecurity threats grow more sophisticated, the tools to defend against them must also evolve. Today, organizations are increasingly relying on data encryption solutions and enterprise data security solutions to stay ahead of modern cyber risks. This blog examines the different types of encryptions, explains the distinction between software- and hardware-based methods, and highlights why physical-key encryption offers one of the most secure options available today.
The Stakes Have Never Been Higher
Data breaches cost organizations billions of dollars each year. Whether it’s ransomware, insider threats, or nation-state cyberattacks, unprotected or poorly encrypted data is a major liability. Encryption is no longer optional—it’s essential.
What Is Encryption?
Encryption converts readable data (plaintext) into unreadable code (ciphertext) using complex mathematical algorithms. Only those with the correct key can decrypt and read the data. It ensures:
- Confidentiality: Only authorized users can access the data.
- Integrity: Data cannot be altered undetected.
- Authentication: Confirms the identity of the sender or device.
Key Encryption Methods and Their Use Cases
Encryption typically involves two types of cryptographic systems:
- Symmetric encryption: Uses the same key to encrypt and decrypt data.
- Asymmetric encryption: Uses a public key to encrypt and a private key to decrypt.
Advanced Encryption Standard (AES)
A fast, secure, and widely adopted encryption standard that operates on 128-bit blocks. AES is known for its strength and efficiency, making it the current encryption benchmark worldwide.
- Type: Symmetric Key
- Standard: AES-128, AES-192, AES-256
- Use: Government, military, enterprise data at rest
RSA (Rivest–Shamir–Adleman)
One of the first public-key cryptosystems, RSA uses a pair of keys (public and private) for encryption and decryption. It is ideal for securely transmitting small amounts of data.
- Type: Asymmetric Key
- Use: Digital signatures, secure emails
Elliptic Curve Cryptography (ECC)
ECC provides strong encryption with shorter key lengths, making it ideal for environments with limited processing power and memory, such as mobile and embedded devices.
- Type: Asymmetric Key
- Use: Mobile and IoT devices
Blowfish and Twofish
Blowfish, developed in 1993, uses a 64-bit block size and variable key lengths, making it fast but less secure for large data volumes. Twofish, its successor, was designed for greater security and uses 128-bit blocks with keys up to 256 bits. While more secure than Blowfish, Twofish is slower and less widely adopted than AES.
- Use: Lightweight encryption for embedded systems or applications with legacy compatibility needs
Software vs Hardware Encryption: What’s the Difference?
| Feature | Software Encryption | Hardware Encryption |
| Where it runs | On system’s CPU | On a dedicated chip |
| Performance | Can slow down system performance | Minimal impact, runs on separate chip |
| Security | Vulnerable to malware and keylogging | Keys stored on hardware, not exposed to OS |
| Ease of deployment | Quick install | Requires specialized enterprise-grade hardware |
Bottom Line: Hardware encryption offers greater isolation, performance, and security.
Physical-Key Encryption is the Ultimate Layer of Defense
Physical encryption keys plug into the device or require keypad input to unlock.
The benefits are:
- Keys are not stored digitally, meaning they can’t be extracted by malware.
- Two-factor authentication by design — you need both the key & access to the system.
- Immune to remote attacks — you can’t hack what isn’t online.
- Perfect for portable storage — ideal in military, healthcare, and forensic fields.
Case Example: Ciphertex SecureNAS® Enterprise
- Uses FIPS 140-2 Level 3 hardware encryption
- Locked/unlocked via physical encryption key
- Designed for U.S. military, healthcare, forensic, and enterprise use
- In over 15 years, Ciphertex SecureNAS systems encryption has never been broken. This track record underscores the effectiveness of physical-key security and Ciphertex’s commitment to uncompromising protection.
What Encryption Should You Use Today?
| Scenario | Recommended Solution |
| Cloud backup | AES-256 with MFA (multi-factor authentication) |
| Portable NAS storage | FIPS-certified hardware encryption + key |
| Remote forensic investigations | Hardware-encrypted system with physical key |
| Internal email communication | ECC + RSA combo |
| IoT deployments | ECC |
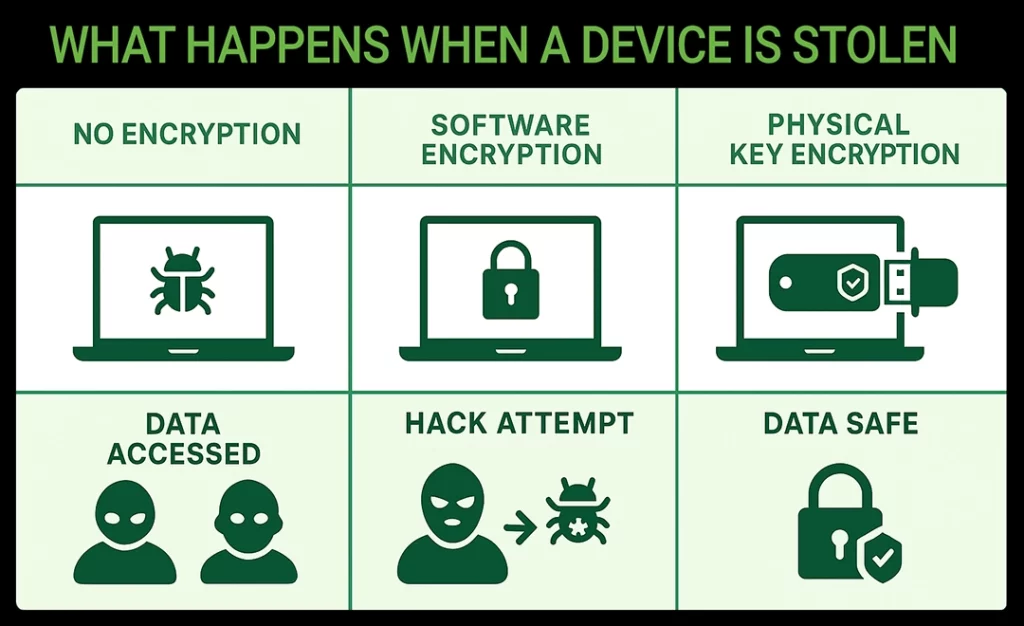
Encryption is evolving alongside threats. While software-based solutions are common and easy to deploy, they are vulnerable. Hardware encryption—especially with physical key security—offers the highest level of protection for organizations that cannot afford to compromise.
Investing in this type of encryption is not just a technical decision—it’s a responsibility to protect what matters most.
About Ciphertex®
Ciphertex Data Security® provides rugged, hardware-encrypted storage solutions engineered for portability, performance, and compliance. As a hardware and software engineering company, they actively customize each solution to match the specific needs and requirements of their customers. Trusted by the U.S. government, military, healthcare, and forensic sectors, Ciphertex SecureNAS® Enterprise is designed to secure the world’s most sensitive data.
Visit: www.ciphertex.com to learn more.